Session Initiation Protocol - SIP
Today I’ll try to remind what SIP is, how it works, and how to integrate it with my Cisco voice Lab.
Originally
designed by Shulzrinne and Handley, SIP, has been standardized in 1996 by IETF with
RFC 3261. It is a widely utilized peer-to-peer telecommunications protocol, and
differently from others, it is open, that is the reason why it is widely used
and implemented.
SIP
introduces some network elements, here explained really shortly :
·
User Agent (UA) : This is a logical SIP endpoint used
to create and manage a SIP session. It can act either as a client (UAC) or as a
server (UAS). A sip phone, or a Softphone can be UAC
·
Proxy Server : An intermediary agent that acts as
UAC or UAS on behalf of other UA in order to establish a SIP session
·
Registrar/Location Server : It’s the server that accepts REGISTER
messages and places the information it receives in those requests into the
location service for the domain it handles.
·
Redirect Server : A UA server that accepts requests
and redirect them to contact an alternate set of URIs.
·
Session Border Controller (SBC) : This is a server usually placed at
the border of a SIP network, used as a bridge between different networks
Basic
messages sent in the SIP environment
- INVITE – connection establishing request
- ACK – acknowledgement of INVITE
by the final message receiver
- BYE – connection termination
- CANCEL – termination of
non-established connection
- REGISTER – UA registration in SIP proxy
- OPTIONS – inquiry of server options
Answers to
SIP messages are in the digital format like in the http protocol. Here
are the most important ones:
- 1XX – information messages (100
– trying, 180 – ringing, 183 – progress)
- 2XX – successful request
completion (200 – OK)
- 3XX – call forwarding, the
inquiry should be directed elsewhere (302 – temporarily moved, 305 – use
proxy)
- 4XX – error (403 – forbidden)
- 5XX – server error (500 –
Server Internal Error, 501 – not implemented)
- 6XX – global failure (606 – Not
Acceptable)
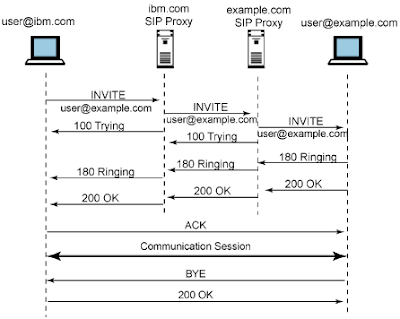
Let’s see
now how a session is established, in order to see which network elements are
involved and which messages are exchanged :
User@ibm.com is the first UA, user@example.com the second one. As we can
see, between them there can be on or more proxy server, that are used to route
the messages from the UAC to the UAS. Further and more detailed explanations of
this flow Is out from the scope of this article.
I really admired your post, such great and useful information that you have mentioned here.
ReplyDeleteVMware Training in Chennai
VMware course in Chennai
Cloud Computing Training in Chennai
Cloud Computing courses in Chennai
Azure Training in Chennai
Microsoft Azure Training in Chennai
DevOps Training in Chennai
AWS Training in Chennai
AWS course in Chennai
Excellent stuff, this is really helpful for beginners and I am glad to visit this page.
ReplyDeleteMicrosoft Windows Azure Training | Online Course | Certification in chennai | Microsoft Windows Azure Training | Online Course | Certification in bangalore | Microsoft Windows Azure Training | Online Course | Certification in hyderabad | Microsoft Windows Azure Training | Online Course | Certification in pune
Great information. It was very useful.
ReplyDeletealso, check CCNA course in Pune